In today's interconnected world, IoT management platform SSH keys free solutions have become indispensable for securing and managing networked devices. As more organizations embrace the Internet of Things (IoT), the need for robust security measures has never been greater. SSH keys play a critical role in ensuring secure access to IoT devices, and understanding how to implement them effectively can significantly enhance your IoT infrastructure's security.
IoT management platforms are at the heart of modern technological advancements, enabling seamless communication between devices. However, with this convenience comes the challenge of ensuring data integrity and device security. This article delves deep into how you can leverage free SSH keys to bolster your IoT management platform's security without compromising on functionality or cost.
Whether you're a tech enthusiast, a small business owner, or an enterprise IT manager, this guide will equip you with the knowledge and tools necessary to harness the power of free SSH keys for your IoT management needs. Let's explore how you can secure your IoT ecosystem while staying within budget.
Read also:Natalie Halcro Baby Daddy Unveiling The Truth And Facts
Table of Contents
- Introduction to IoT Management Platforms
- Understanding SSH Keys
- Benefits of Using Free SSH Keys
- Steps to Implement Free SSH Keys
- Best Practices for SSH Key Security
- Common Challenges and Solutions
- Real-World Case Studies
- Tools and Resources for Free SSH Keys
- Comparison with Paid SSH Key Solutions
- Future Trends in IoT Management and SSH Keys
Introduction to IoT Management Platforms
IoT management platforms serve as the backbone of interconnected systems, enabling centralized control and monitoring of IoT devices. These platforms provide a range of functionalities, from device provisioning and firmware updates to data analytics and security management. As the number of IoT devices grows exponentially, managing them efficiently becomes increasingly complex.
One of the critical aspects of IoT management is ensuring secure communication between devices. This is where SSH keys come into play. By leveraging SSH keys, organizations can authenticate devices and establish encrypted connections, thereby safeguarding sensitive data and preventing unauthorized access.
IoT management platform SSH keys free solutions offer a cost-effective way to implement these security measures without the need for expensive proprietary software. This makes them an attractive option for businesses of all sizes looking to enhance their IoT security posture.
Understanding SSH Keys
What Are SSH Keys?
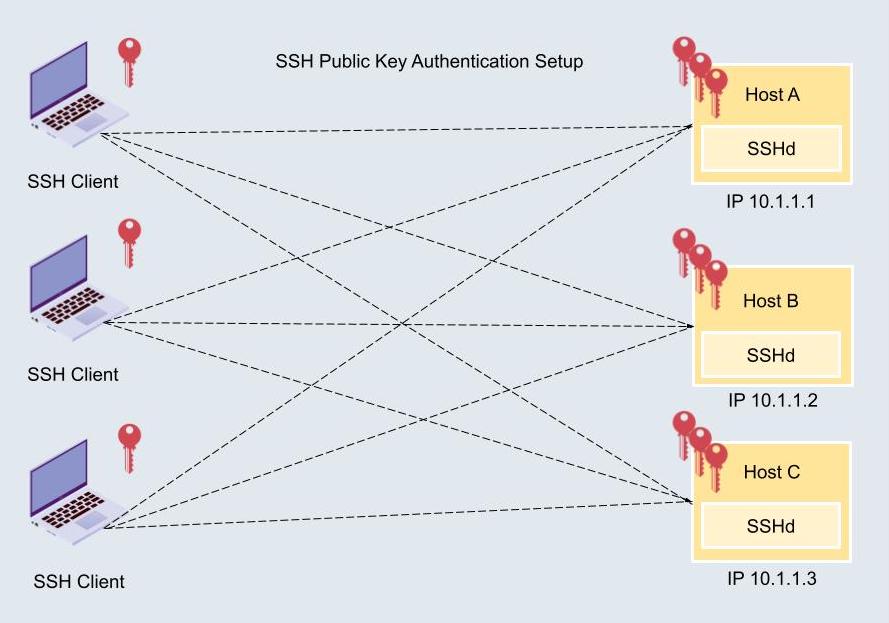
SSH (Secure Shell) keys are a pair of cryptographic keys used for authenticating secure connections between devices. They consist of a public key, which is shared with the server or device, and a private key, which remains confidential and is used to decrypt data sent by the server.
SSH keys are widely used in IT infrastructure for secure remote access, automated processes, and inter-device communication. In the context of IoT management platforms, they provide an additional layer of security by replacing traditional password-based authentication with more secure key-based authentication.
How Do SSH Keys Work?
The process begins with generating a key pair using an SSH client. The public key is then uploaded to the IoT management platform or device, while the private key is securely stored on the user's machine. When a connection is initiated, the server verifies the public key and sends a challenge to the client, which responds using the private key. If the response matches, the connection is established.
Read also:Laura Stroud Rising Star In The Entertainment World
This method eliminates the need for passwords, reducing the risk of brute-force attacks and unauthorized access.
Benefits of Using Free SSH Keys
Opting for IoT management platform SSH keys free solutions offers several advantages:
- Cost-Effective: Free SSH keys eliminate the need for purchasing expensive licenses or subscriptions, making them ideal for budget-conscious organizations.
- Enhanced Security: Key-based authentication is significantly more secure than password-based methods, reducing the likelihood of unauthorized access.
- Scalability: Free SSH keys can be easily implemented across multiple devices, making them suitable for large-scale IoT deployments.
- Community Support: Many free SSH tools come with active communities and extensive documentation, ensuring you have access to support and resources when needed.
Steps to Implement Free SSH Keys
Step 1: Generate SSH Key Pair
Begin by generating an SSH key pair using a tool like OpenSSH. Open a terminal or command prompt and run the following command:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"
This command generates a 4096-bit RSA key pair and associates it with your email address for identification purposes.
Step 2: Add Public Key to IoT Management Platform
Once the key pair is generated, copy the public key (usually located in ~/.ssh/id_rsa.pub) and add it to your IoT management platform. Most platforms provide a straightforward interface for uploading public keys.
Step 3: Test the Connection
After adding the public key, test the connection to ensure everything is working correctly. Use the following command to connect to your IoT device:
ssh username@device_ip
If the connection is established without prompting for a password, the setup is successful.
Best Practices for SSH Key Security
While SSH keys enhance security, they must be managed properly to avoid potential vulnerabilities. Follow these best practices:
- Use Strong Keys: Generate keys with a sufficient bit length (e.g., 4096-bit RSA or ECC keys) to ensure robust encryption.
- Protect Private Keys: Store private keys in a secure location and use passphrase protection to add an extra layer of security.
- Regularly Rotate Keys: Periodically replace old keys with new ones to minimize the risk of compromise.
- Limit Key Access: Restrict access to private keys to authorized personnel only and avoid sharing them unnecessarily.
Common Challenges and Solutions
Challenge: Key Management Complexity
As the number of devices grows, managing SSH keys can become cumbersome. To address this, consider using SSH key management tools that automate key generation, distribution, and revocation.
Challenge: Key Theft
If a private key is compromised, it can lead to unauthorized access. To mitigate this risk, implement strict access controls and regularly audit key usage.
Real-World Case Studies
Case Study 1: Small Business IoT Deployment
A small retail chain implemented free SSH keys to secure their IoT-based inventory management system. By leveraging open-source tools, they achieved robust security without incurring additional costs, resulting in improved operational efficiency and reduced downtime.
Case Study 2: Enterprise IoT Network
A large manufacturing company adopted IoT management platform SSH keys free solutions to secure their industrial IoT network. The implementation streamlined device authentication and reduced the risk of cyberattacks, enhancing overall network resilience.
Tools and Resources for Free SSH Keys
Several tools and resources are available to help you implement free SSH keys effectively:
- OpenSSH: A widely used open-source SSH implementation that supports key generation and management.
- SSHKeychain: A macOS tool for managing SSH keys securely.
- GitHub Guides: Comprehensive documentation and tutorials on SSH key usage and best practices.
Comparison with Paid SSH Key Solutions
While paid SSH key solutions offer additional features like centralized management and advanced analytics, free options can still meet the needs of many organizations. The decision to choose between free and paid solutions depends on factors such as budget, scalability requirements, and specific security needs.
For small to medium-sized businesses, IoT management platform SSH keys free solutions often provide sufficient functionality at no cost. Larger enterprises may benefit from the enhanced capabilities of paid options but should carefully evaluate their return on investment.
Future Trends in IoT Management and SSH Keys
As IoT continues to evolve, so do the technologies and practices surrounding its management. Emerging trends include:
- Quantum-Resistant Cryptography: With the advent of quantum computing, researchers are developing new cryptographic methods to ensure long-term security.
- AI-Driven Key Management: Artificial intelligence is being used to automate and optimize SSH key management processes, reducing human error and improving efficiency.
- Blockchain for Key Storage: Blockchain technology offers a decentralized and tamper-proof way to store and manage SSH keys, enhancing security and transparency.
Conclusion
In conclusion, IoT management platform SSH keys free solutions provide a powerful and cost-effective way to secure your IoT infrastructure. By following the steps outlined in this guide and adhering to best practices, you can implement robust security measures that protect your devices and data from potential threats.
We encourage you to take action by exploring the tools and resources mentioned in this article and sharing your experiences in the comments below. Your feedback helps us improve and refine our content. Additionally, feel free to explore other articles on our site for more insights into IoT management and cybersecurity.