In today's interconnected world, finding the best SSH RemoteIoT free solutions has become essential for both individuals and businesses. Secure Shell (SSH) plays a crucial role in ensuring safe and encrypted communication between devices. This article delves deep into the realm of SSH RemoteIoT, exploring free options that provide robust security without breaking the bank.
Whether you're a tech enthusiast or a professional managing remote IoT devices, understanding SSH RemoteIoT is vital. This technology enables secure access to devices over the internet, protecting sensitive data from unauthorized access. With the rise of IoT devices, the demand for secure remote management has skyrocketed.
This guide aims to provide comprehensive insights into the best SSH RemoteIoT free solutions available. We will cover everything from basic concepts to advanced configurations, ensuring you have all the tools needed to make an informed decision.
Read also:Anthony Kiedis Abuse The Struggles Recovery And Legacy
Table of Contents
- What is SSH RemoteIoT?
- The Importance of SSH in IoT
- Best SSH RemoteIoT Free Options
- Setting Up SSH for IoT Devices
- Security Considerations for SSH RemoteIoT
- Troubleshooting Common SSH Issues
- Comparison of SSH Clients
- Optimizing SSH Performance
- The Future of SSH RemoteIoT
- Conclusion
What is SSH RemoteIoT?
SSH RemoteIoT refers to the use of Secure Shell (SSH) protocols to manage and interact with IoT devices remotely. SSH provides a secure channel for communication, encrypting data exchanged between devices and preventing unauthorized access. With the proliferation of IoT devices, SSH has become an indispensable tool for ensuring secure remote management.
Key Features of SSH RemoteIoT
Here are some of the key features that make SSH RemoteIoT a preferred choice:
- Encrypted communication
- Authentication mechanisms
- Support for multiple devices
- Scalability for enterprise-level solutions
The Importance of SSH in IoT
As the Internet of Things (IoT) continues to expand, the importance of SSH in securing remote connections cannot be overstated. IoT devices often operate in unsecured environments, making them vulnerable to cyber threats. SSH provides a layer of protection by encrypting data and ensuring only authorized users can access the devices.
Benefits of Using SSH in IoT
Below are the benefits of integrating SSH into your IoT infrastructure:
- Enhanced security through encryption
- Reduced risk of data breaches
- Improved device management
- Cost-effective solution for remote access
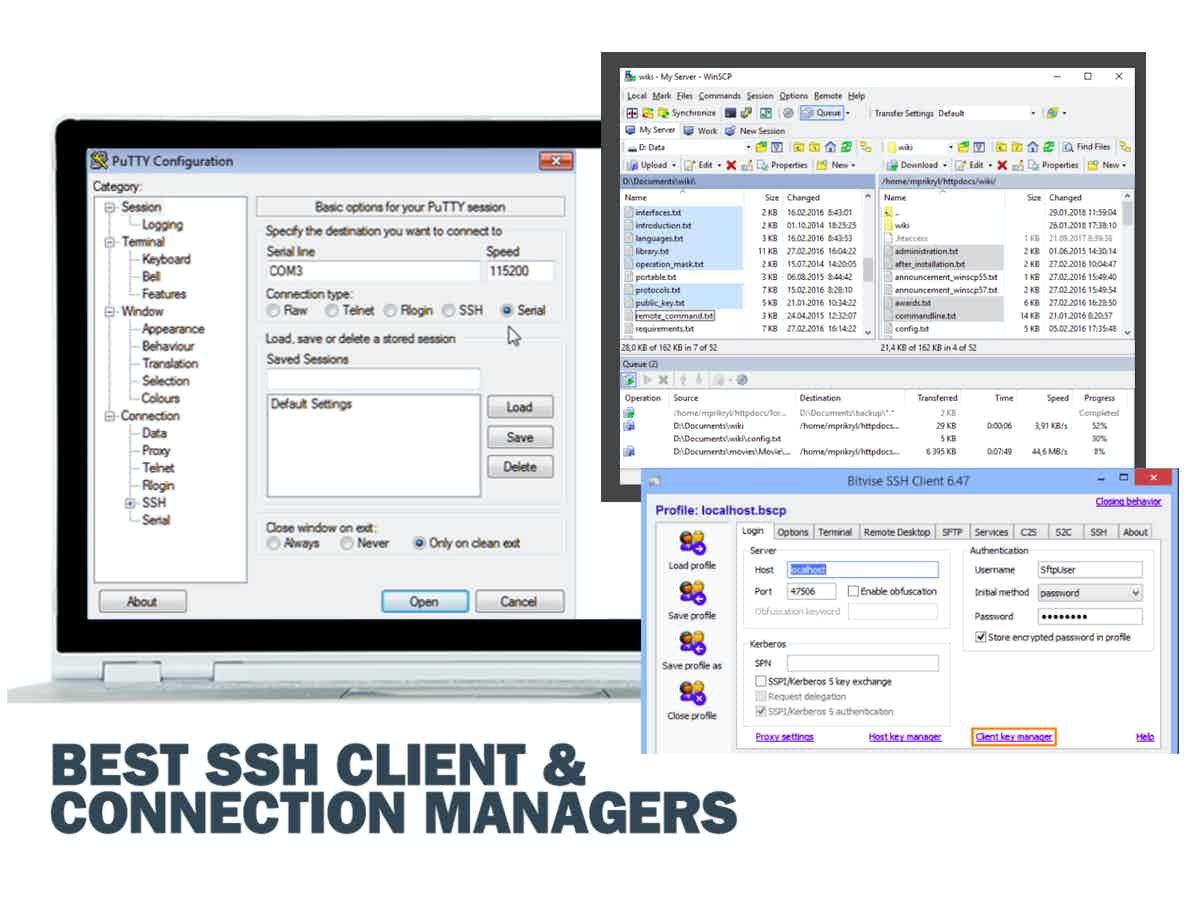
Best SSH RemoteIoT Free Options
Several SSH RemoteIoT free solutions are available, each offering unique features and capabilities. Below are some of the top options:
1. OpenSSH
OpenSSH is one of the most popular SSH implementations, widely used for securing remote connections. It offers robust security features and is compatible with a wide range of devices. OpenSSH is available for free and is supported by a large community of developers.
Read also:Tonya Hartwell The Remarkable Journey Of An Inspirational Figure
2. PuTTY
PuTTY is a widely used SSH client for Windows users. It provides a simple interface for connecting to remote devices and supports various protocols, including SSH. PuTTY is available for free and is highly customizable, making it a favorite among users.
3. Bitvise SSH Client
Bitvise SSH Client is another excellent option for those looking for a free SSH solution. It offers advanced features such as tunneling and file transfer, making it ideal for managing IoT devices. Bitvise is available for free for personal use, with additional features available for purchase.
Setting Up SSH for IoT Devices
Setting up SSH for IoT devices involves several steps, including configuring the server, generating keys, and establishing a secure connection. Below is a step-by-step guide to help you get started:
Step 1: Install SSH Server
Begin by installing an SSH server on your IoT device. Most Linux-based devices come with OpenSSH pre-installed, but you may need to enable it manually.
Step 2: Generate SSH Keys
Generating SSH keys is a crucial step in ensuring secure authentication. Use the following command to generate a key pair:
ssh-keygen -t rsa -b 4096
Step 3: Establish a Connection
Once the server is configured and keys are generated, you can establish a connection using an SSH client. Use the following command to connect:
ssh username@device_ip
Security Considerations for SSH RemoteIoT
While SSH provides a secure channel for communication, there are several security considerations to keep in mind:
1. Use Strong Passwords
Ensure that all user accounts have strong, complex passwords to prevent brute-force attacks.
2. Enable Key-Based Authentication
Key-based authentication is more secure than password-based authentication and should be enabled whenever possible.
3. Regularly Update Software
Keep your SSH server and client software up to date to protect against vulnerabilities.
Troubleshooting Common SSH Issues
Encountering issues while using SSH is not uncommon. Below are some common problems and their solutions:
Problem 1: Connection Timeout
Solution: Check your network settings and ensure that the SSH port (default is 22) is open and accessible.
Problem 2: Authentication Failure
Solution: Verify that your SSH keys are correctly configured and that the username and password are correct.
Comparison of SSH Clients
Choosing the right SSH client can significantly impact your experience. Below is a comparison of some popular SSH clients:
| Client | Platform | Features | Cost |
|---|---|---|---|
| OpenSSH | Linux, macOS | Secure, open-source | Free |
| PuTTY | Windows | User-friendly, customizable | Free |
| Bitvise | Windows | Advanced features, tunneling | Free (personal use) |
Optimizing SSH Performance
To ensure optimal performance of your SSH RemoteIoT setup, consider the following tips:
1. Use Compression
Enabling compression can improve data transfer speeds, especially over slow connections.
2. Limit Connections
Restrict the number of simultaneous connections to prevent overloading the server.
3. Monitor Logs
Regularly monitor SSH logs to detect and address potential security threats.
The Future of SSH RemoteIoT
The future of SSH RemoteIoT looks promising, with advancements in technology driving innovation. As IoT devices become more integrated into everyday life, the demand for secure remote management solutions will continue to grow. Expect to see improvements in encryption, automation, and user experience in the coming years.
Conclusion
Choosing the best SSH RemoteIoT free solution requires careful consideration of your needs and the features offered by each option. This guide has provided a comprehensive overview of SSH RemoteIoT, covering everything from basic concepts to advanced configurations. By following the tips and recommendations outlined here, you can ensure secure and efficient management of your IoT devices.
Call to Action: Share your thoughts and experiences with SSH RemoteIoT in the comments below. Have you tried any of the solutions mentioned in this article? Let us know how they worked for you. For more insightful content, explore our other articles on technology and cybersecurity.
References: