Accessing IoT devices through SSH for free is a growing trend among tech enthusiasts and professionals alike. Secure Shell (SSH) provides an encrypted and secure way to connect to Internet of Things (IoT) devices remotely, making it a crucial tool for managing and monitoring smart devices. This guide will explore the possibilities of accessing IoT devices via SSH without incurring costs, while ensuring security and efficiency.
As the Internet of Things (IoT) continues to expand, businesses and individuals are increasingly looking for ways to manage their devices remotely. Free SSH access can help bridge this gap by providing a cost-effective solution for remote management. However, understanding the nuances of SSH and IoT is essential to ensure secure and reliable connectivity.
This article will delve into the technical aspects of accessing IoT devices through SSH, including the setup process, security considerations, and tools available for free use. Whether you're a beginner or an experienced user, this guide will equip you with the knowledge needed to harness the power of SSH for IoT applications.
Read also:Juliana Palvin A Rising Star In The Entertainment Industry
Understanding IoT and SSH: The Basics
To fully grasp the concept of accessing IoT devices via SSH, it's important to understand the basics of both IoT and SSH. IoT refers to the network of physical objects embedded with sensors, software, and connectivity, enabling them to exchange data with other devices and systems. SSH, on the other hand, is a cryptographic network protocol that facilitates secure communication between devices.
What Is IoT?
The Internet of Things (IoT) has revolutionized the way we interact with technology. IoT devices range from smart home appliances to industrial sensors, all designed to enhance convenience, efficiency, and productivity. These devices collect and transmit data, creating a vast ecosystem of interconnected systems.
What Is SSH?
Secure Shell (SSH) is a protocol used to securely connect to remote devices over an unsecured network. It encrypts data during transmission, ensuring that sensitive information remains private and secure. SSH is widely used in IT infrastructure for managing servers, routers, and other network devices.
Why Access IoT Devices via SSH?
Accessing IoT devices via SSH offers several advantages, including enhanced security, remote management capabilities, and cost efficiency. By leveraging SSH, users can ensure that their IoT devices remain secure and functional, even when accessed from remote locations.
- Enhanced Security: SSH encrypts all communication between devices, protecting against unauthorized access and data breaches.
- Remote Management: SSH allows users to manage IoT devices from anywhere in the world, providing flexibility and convenience.
- Cost Efficiency: Free SSH access eliminates the need for expensive proprietary solutions, making it an attractive option for budget-conscious users.
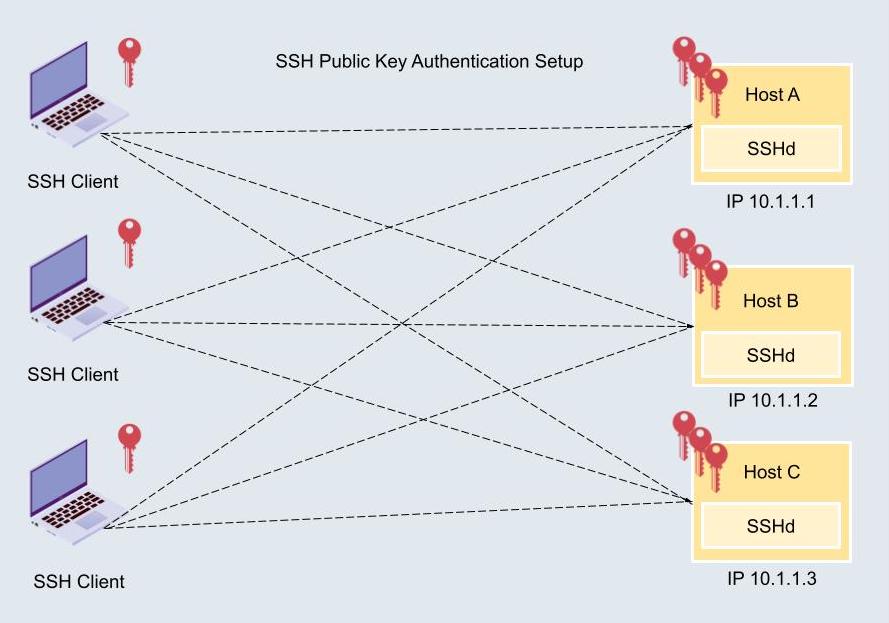
Setting Up Free SSH Access for IoT Devices
Setting up SSH access for IoT devices can seem daunting, but with the right tools and knowledge, it can be a straightforward process. Below are the steps to configure SSH on your IoT devices:
Step 1: Enable SSH on Your IoT Device
Most IoT devices come with SSH functionality built-in. To enable SSH, follow these steps:
Read also:Who Is Shaboozeys Wife Exploring The Life And Story Behind The Scenes
- Access the device's settings menu.
- Locate the network or security section.
- Enable SSH and note the port number (usually 22).
Step 2: Install an SSH Client
To connect to your IoT device via SSH, you'll need an SSH client. Popular options include:
- PuTTY: A free and widely used SSH client for Windows.
- Terminal: Built into macOS and Linux systems, providing a native SSH client.
- Mobile Apps: SSH clients are available for both Android and iOS devices, allowing remote access on the go.
Step 3: Connect to Your IoT Device
Once SSH is enabled on your device and you have an SSH client installed, you can establish a connection. Use the following command in your SSH client:
ssh username@IP_address
Replace "username" with your IoT device's username and "IP_address" with the device's IP address. You'll be prompted to enter a password or use a private key for authentication.
Security Considerations for IoT SSH Access
While SSH provides a secure method for accessing IoT devices, it's essential to implement additional security measures to protect against potential threats. Below are some best practices for securing your IoT SSH access:
- Use Strong Passwords: Ensure that all accounts on your IoT devices have strong, unique passwords.
- Enable Two-Factor Authentication (2FA): Add an extra layer of security by requiring a second form of verification.
- Restrict Access: Limit SSH access to trusted IP addresses or networks to prevent unauthorized connections.
- Regularly Update Firmware: Keep your IoT devices up to date with the latest firmware to address known vulnerabilities.
Free Tools for IoT SSH Access
Several free tools are available to facilitate SSH access for IoT devices. These tools offer a range of features, from basic connectivity to advanced monitoring capabilities. Some popular options include:
1. OpenSSH
OpenSSH is an open-source SSH client and server software that provides secure communication between devices. It's widely regarded as one of the most reliable and secure SSH solutions available.
2. Tera Term
Tera Term is a free SSH client that supports multiple protocols, including SSH, Telnet, and serial communication. Its user-friendly interface makes it an ideal choice for beginners and professionals alike.
3. KiTTY
KiTTY is a lightweight SSH client based on PuTTY, offering enhanced features and improved performance. It's particularly well-suited for managing multiple SSH connections simultaneously.
Best Practices for Managing IoT Devices via SSH
Effectively managing IoT devices via SSH requires adherence to best practices to ensure optimal performance and security. Below are some tips for managing IoT devices using SSH:
- Monitor Activity Logs: Regularly review SSH activity logs to detect and respond to suspicious behavior.
- Automate Tasks: Use SSH scripts to automate repetitive tasks, saving time and reducing the risk of human error.
- Implement Role-Based Access Control (RBAC): Assign specific permissions to users based on their roles to prevent unauthorized access.
Common Challenges in IoT SSH Access
While SSH provides a powerful tool for managing IoT devices, several challenges can arise during implementation. Below are some common issues and solutions:
1. Connectivity Issues
Connectivity problems can occur due to network configuration errors or firewall restrictions. Ensure that your network settings allow SSH traffic and that firewalls are properly configured.
2. Authentication Failures
Authentication failures may result from incorrect usernames, passwords, or private keys. Double-check your credentials and ensure that they match the device's settings.
3. Performance Bottlenecks
Heavy workloads can lead to performance bottlenecks, impacting the responsiveness of your IoT devices. Optimize your SSH configuration and consider upgrading hardware if necessary.
Data and Statistics Supporting IoT SSH Access
According to a report by Gartner, the number of IoT devices is expected to reach 25 billion by 2030, highlighting the growing importance of secure connectivity solutions like SSH. Additionally, a survey conducted by IoT Analytics revealed that 70% of enterprises prioritize security when implementing IoT solutions, underscoring the critical role of SSH in ensuring secure access.
Conclusion and Call to Action
Accessing IoT devices via SSH for free offers a secure and cost-effective solution for managing smart devices remotely. By following the steps outlined in this guide, you can set up and maintain SSH connections with confidence, ensuring the security and efficiency of your IoT ecosystem.
We encourage you to share your experiences and insights in the comments section below. Additionally, feel free to explore our other articles for more information on IoT, SSH, and related technologies. Together, let's build a safer and smarter connected world!
Table of Contents
- Understanding IoT and SSH: The Basics
- Why Access IoT Devices via SSH?
- Setting Up Free SSH Access for IoT Devices
- Security Considerations for IoT SSH Access
- Free Tools for IoT SSH Access
- Best Practices for Managing IoT Devices via SSH
- Common Challenges in IoT SSH Access
- Data and Statistics Supporting IoT SSH Access
- Conclusion and Call to Action